Cracker Tools 2013, Pentest Tool 2013, Security Tools, 2013, Password Hack 2013, which might be useful for you can use in 2013. Happy Hacking All :)

Come game download penetration testing and security tools 2013, 2013, 2013 networking tools, gmail hacking tools 2013, learn ethical hacking, 2013, 2013 vulnerability assessment, penetration testing, 2013, 2013 email hacking, password hacking, 2013, reverse engineering, 2013. Download hacking tools, networking tools, gmail hacking, learn ethical hacking, vulnerability, penetration testing, email hack, hacking, password hacking, reverse engineering, 2013, wifi hacker 2013. Hacker Tools 2013, Hack Tool, 2013, 2013 Hacker Tool, Hacking Tool 2013, Hack Tool 2013, Cracking Tools 2013, Cracker Tools 2013, Cracking Tool 2013, Cracker Tool 2013, 2013 Tools Crack, Crack Tool 2013, Security Tool 2013, pentester Tool 2013, 2013 Password Cracker, Password Hacking 2013.
1. PWN STAR
A bash script to launch the AP, can be configured with a variety of attack options. Including a php script and server index.html, for phishing. Can act as a multi-client captive portal using php and iptables. Exploitation classics such as crime-PDF, De-auth with aireplay, etc..

General Features:
Managing Interfaces and MAC Spoofing
Set sniffing
Phishing Web
Karmetasploit
WPA handshake
De-auth client
Managing IptablesDownload PwnStar Here:

2. ZED Attack Proxy (ZAP)(ZAP) is an integrated penetration testing tool for finding vulnerabilities in web applications. This tool is designed for use by people with a variety of security experience and as such is ideal for developers and functional testers who are new to penetration testing as well as being a useful addition to the toolbox tester.

Key Features:
Intercepting Proxy
Active scanners
Passive scanners
Brute Force scanner
Spider
Fuzzer
Port Scanner
Dynamic SSL certificates
API
Beanshell integrationDownload ZAP Here:

3. SET (Social Engineering Toolkit)
Tools that focus on attacking the human element of weakness and inadvertence. This tool is widely used today and is one of the most successful tools demonstrated at Defcon.
Key Features:
Spear-Phishing Attack Vector
Java Applet Attack Vector
Metasploit Browser Exploit Method
Credential Harvester Attack Method
Tabnabbing Attack Method
Man Left in the Middle Attack Method
Web Jacking Attack Method
Multi-Attack Web Vector
Infectious Media Generator
Teensy USB HID Attack Vector
Download Social Engineering Toolkit Here:

4. Burp SuiteBurp Suite is a very nice tool for web application security testing. This tool is great for pentester and security researchers. It contains a variety of tools with many interfaces between them designed to facilitate and accelerate the process of web application attacks.

General Function:
Interception proxies
Radar and spiders crawling
Webapps scanner
Tool assault
Repeater and sequencer toolsDownload Burp Suite Here:

5. EttercapEttercap is a multipurpose sniffer / interceptor / logger for Local Area Network. It supports active and passive dissection of many protocols (even in code) and includes many feature for network and host analysis.
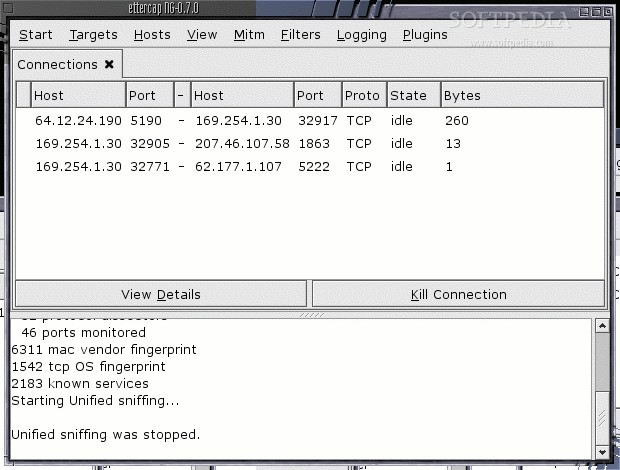
General Function:
To capture traffic and data
To do logging network
Etc.Download Ettercap Here:

6. SANS Investigative Forensic Toolkit (SIFT)The SANS Investigative Forensic Toolkit (SIFT) Workstation is a VMware Appliance that can be configured with all the requirements to perform a detailed digital forensic. Compatible with Expert Witness Format (E01), Advanced Forensic Format (AFF), and raw (dd) evidence formats. The new version has been completely rebuilt on the Ubuntu base with many additional tools and capabilities that are used in modern technology forensik.
 General Function SIFT:
General Function SIFT:iPhone, Blackberry, and Android Forensic Capabilities
Registry Viewer (YARU)
Compatibility with F-Response Tactical, Standard, and Enterprise
PTK 2.0 (Special Release - Not Available for Download)
Automated Generation Timeline via log2timeline
Many Firefox Investigative Tools
Windows Journal Parser and Shellbags Parser (jp and sbag)
Many Windows Analysis Utilities (prefetch, usbstor, event logs, and more)
Complete Overhaul of Regripper Plugins (added over 80 additional plugins)
Download SANS Investigative Forensic Toolkit (SIFT) Here:

7. WiresharkWireshark is the most widely used and most popular in the world the protocol analyzer, and is the de facto standard across many industries and educational institutions to analyze the network in different protocol.

General Function:
Live capture and offline analysis
Standard three-pane packet browser
Multi-platform: Runs on Windows, Linux, OS X, Solaris, FreeBSD, NetBSD, and many others
Captured data network can be browsed via a GUI, or via the TTY-mode tshark utility
The most powerful display filters in the industry
Rich VoIP analysis
Read / write many different capture file formats
Etc.Download WireShark Here:

8. WEBSPLOITWebSploit is Open Source Project for Remote Scan and Analysis System of the weaknesses in web applications.
Key Features:[>] Social Engineering Works[>] Scan, Web Crawler & Analysis[>] Automatic Exploiter[>] Support Network Attacks-[+] Autopwn - Used From Metasploit Exploit For Scan and Target Service[+] WMAP - Scan, Target Used Crawler From Metasploit WMAP plugin[+] Format infector - inject the payload into reverse and bind file format[+] Phpmyadmin Scanner[+] LFI Bypasser[+] Apache Scanner Users[+] Dir Bruter[+] Admin finder[+] MLITM Attack - Man Left In The Middle, XSS Phishing Attacks[+] MITM - Man In The Middle Attack[+] Java Applet Attack[+] Attack Vector MFOD[+] USB Infection Attack[+] Dos ARP Attack[+] Attack Killer App[+] Attack Fake Update[+] Fake Access Point Attack
Download WebSploit Framework Here:

9. WINAUTOPWNWinAutoPWN is a tool that is used to exploit the Windows Framework directly, so that we are automatically going to be an administrator on the windows. Widely used by "Defacer" Indonesia to deface the Windows Server :)

Download WinAutoPWN Here:

10. HASHCATHashcat are a variety of tools to crack passwords in encrypted, it is very powerful for password recovery.
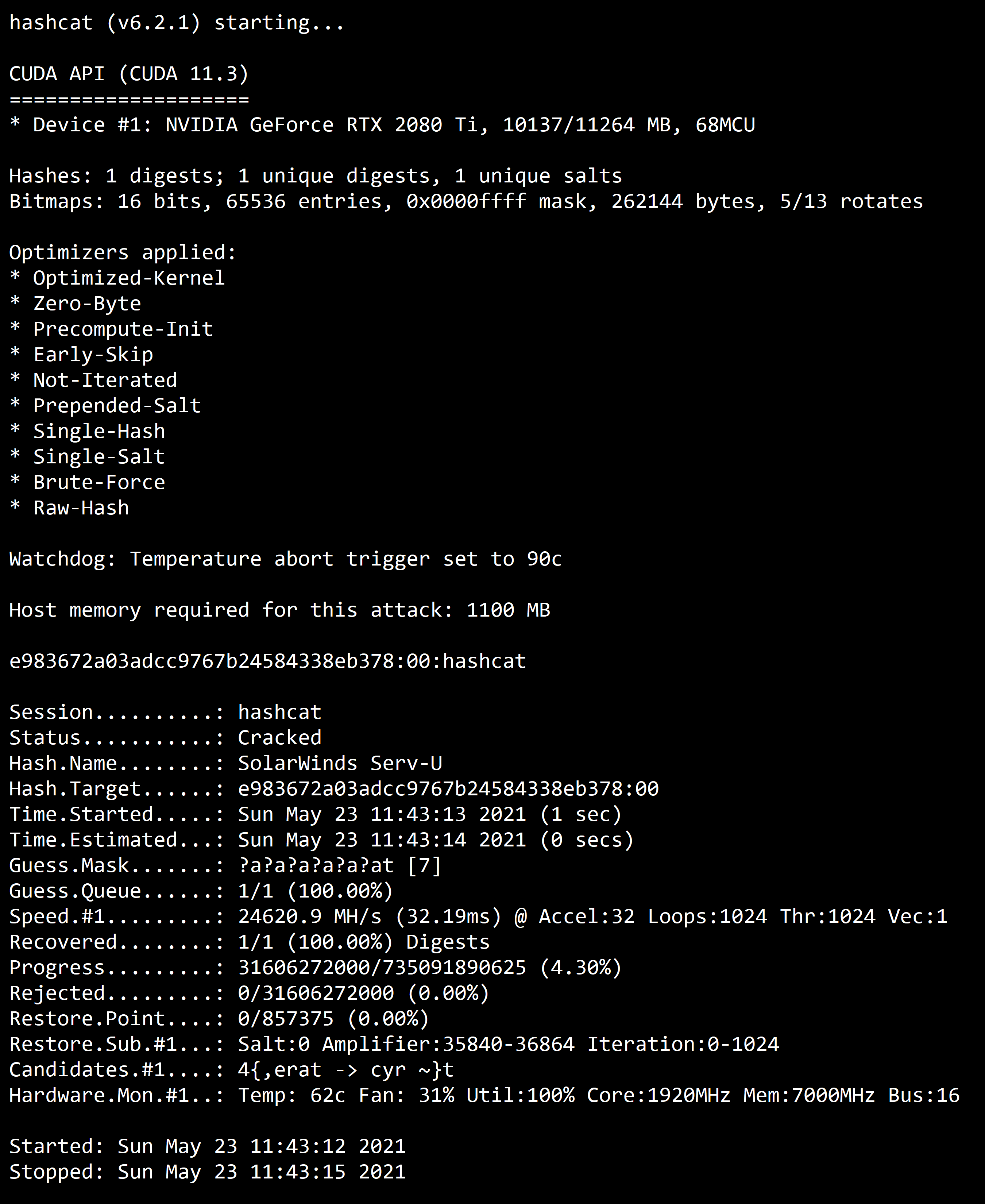
Download HashCat Here:

11. UniscanUniscan is a scanner for web applications, written in perl for Linux. Currently Uniscan version is 6.2.

General Function:
Identification of system pages through a Web Crawler.
Use of threads in the crawler.
Control the maximum number of requests the crawler.
Control of variation of system pages identified by Web Crawler.
Control of file extensions that are ignored.
Test of pages found via the GET method.
Test the forms found via the POST method.
Support for SSL requests (HTTPS).
Proxy support.
Generate site list using Google.
Generate site list using Bing.
Plug-in support for Crawler.
Plug-in support for dynamic tests.
Plug-in support for static tests.
Plug-in support for stress tests.
Multi-language support.
Web client.Download Uniscan Here:

12. OLYYDBGOllyDbg is a 32-bit assembler debugger for Microsoft Windows. Emphasis on binary code analysis makes it particularly useful in cases where source code is not available.

General Function:
Intuitive user interface, no cryptical commands
Code analysis - traces registers, recognizes procedures, loops, API calls, switches, tables, constants and strings
Directly loads and debugs DLLs
Object file scanning - locates routines from object files and libraries
Allows for user-defined labels, comments and function descriptions
Understands debugging information in Borland ® format
Saves patches between sessions, writes them back to executable file and updates fixups
Open architecture - many third-party plugins are available
No installation - no trash in registry or system directories
Debugs multithreaded applications
Attaches to running programs
Configurable disassembler, supports both MASM and IDEAL formats
MMX, 3DNow! and SSE instructions and the data types, Including Athlon extensions
Full UNICODE support
Dynamically recognizes ASCII and UNICODE strings - also in Delphi format!
Recognizes complex code constructs, like call to jump to procedure
Decodes calls to more than 1900 standard API and 400 C functions
Gives context-sensitive help on API functions from external help file
Sets conditional, logging, memory and hardware breakpoints
Traces program execution, logs arguments of known functions
Shows fixups
Dynamically traces stack frames
Searches for imprecise commands and masked binary sequences
Searches whole allocated memory
Finds references to constant or address range
Examines and modifies memory, sets breakpoints and Pauses program on-the-fly
Assembles commands into the shortest binary form
Starts from the floppy diskDownload Ollydbg Here:

13. BBQSQLBBQSQL an Opensource SQL injection tools with the framework specifically designed to carry out the process in hyper fast, database agnostic, easy to setup, and easy to modify. This is another amazing release from Arsenal Blackhat USA 2012. When conducting security assessments of applications, we often find that it is difficult to SQL vulnerabilities exploitable, with this tool will be extremely easy.BBQSQL written in the Python programming language. This is very useful when complex SQL injection attack vulnerabilities. BBQSQL also a semi-automated tool, which allows little customization for those who are finding it difficult to trigger a SQL injection. The tool is built to be database agnostic and very versatile. It also has an intuitive UI for setting up the attack much easier.

General Function:
SQL Injection Tools
URL
HTTP Method
Headers
Cookies
Encoding methods
Redirect behavior
Files
HTTP Auth
ProxiesDownload BBQSQL Here:

14. CRYPTOHAZETools to crack password / hash where cryptohaze supports CUDA, OpenCL, and the CPU code (SSE, AVX, etc.). Can run on OS that support CUDA. These are intended to make it easier to pentester did crack the hash.

General Function:
Crack various kinds of hash
Showing results from crackhash
Cracking on various OS platformsDownload Cryptohaze Here:

15. SAMURAI WEB TESTING FRAMEWORK (SWTF)SWTF is used to do testing / pentest against web application, is used to find a weakness and exploited to perform web. Very comprehensive and widely used in the world.

General Function:
Web Scanner
Web Mapping
Web ExploitationDownload The Samurai Web Testing Framework Here:

Tools on the mandatory to have in 2013, survived to try and experiment in the early years
Thanks. Michael Webster


No comments:
Post a Comment